Open-source vulnerability assessment tools are effective security scanners to detect missing patches, misconfiguration, and other vulnerabilities. These scanners also publish their code publicly and provide a free version with most, if not all, features. To help you select the best tool, we picked the top two tools in each of three categories: devices (endpoints, routers, containers, etc.), websites and applications (aka web and app), and specialty scanners for specific assets.
Here are the six best open-source vulnerability scanners:
- Nmap: Best device scanner overall
- OpenVAS: Best device scanner for user experience
- ZAP: Best web and app scanner overall
- OSV-Scanner: Best web and app scanner for library dependency
- CloudSploit: Best specialty scanner for cloud and containers
- sqlmap: Best specialty scanner for databases
Table of Contents
Featured Partners: Vulnerability Management Software
Top Open-Source Vulnerability Scanner Software Comparison
The table below briefly compares the top six tools and provides the overall rating in comparison with the other vulnerability scanning tools (aka vulnscanners) on the list, the types of assets scanned, and the availability of premium support or commercial versions of the tool.
| Overall Rating | Device Scanning | Website & Application Scanning | Specialty | Paid Support Option | |
|---|---|---|---|---|---|
| Nmap | 4.4 | ✔️ | ❌ | Port scanning | ❌ |
| OpenVAS | 4.3 | ✔️ | ❌ | ❌ | ✔️ |
| ZAP | 4.6 | ❌ | ✔️ | ❌ | ✔️ |
| OSV-Scanner | 4.0 | ❌ | ✔️ | Library dependency | ❌ |
| CloudSploit | 3.9 | Cloud and container only | ❌ | Cloud and container | ❌ |
| sqlmap | 3.8 | ❌ | Databases only | Databases | ❌ |
Although we used a single scale to evaluate all open-source vulnerability scanners, they can’t be used interchangeably. For example, the best device scanning tool, Nmap, can only perform very limited application scanning, and the best web and app scanning tool, ZAP, can’t scan devices for vulnerabilities. Explore the detailed reviews of each tool for more context and read our rating methodology below.
Nmap – Best Device Scanner Overall
Overall Rating: 4.4/5
- Open-source value: 4.5/5
- Core scanning features: 4.2/5
- Ease of use: 4.7/5
- User support: 3.8/5
Nmap scores the highest for core scanning features and highest overall for device scanners thanks to the huge number of devices it can scan. The list well exceeds traditional network security port scans to include cloud infrastructure, Internet of Things (IoT), and even some website applications. Hackers also frequently use the tool, so security pros often use Nmap even if they already own commercial tools to ensure they capture the hacker’s perspective.

Pros
Cons
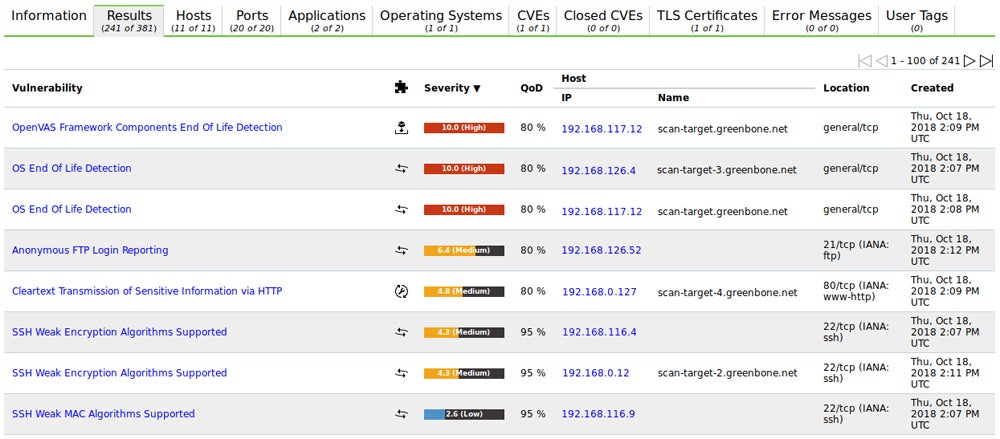
OpenVAS – Best Device Scanner for User Experience
Overall Rating: 4.3/5
- Open-source value: 4.9/5
- Core scanning features: 4.1/5
- Ease of use: 4.3/5
- User support: 4.8/5
OpenVAS places first for user support primarily thanks to an effective graphic user interface (GUI) and an option for premium customer support. Yet it also enjoys a large community of industry users, inclusion in cybersecurity certification training, and built-in compliance reports. Greenbone maintains a strong threat feed and the scanning capabilities for the tool originally forked off of Nessus, now a closed-source commercial product by Tenable.

Pros
Cons
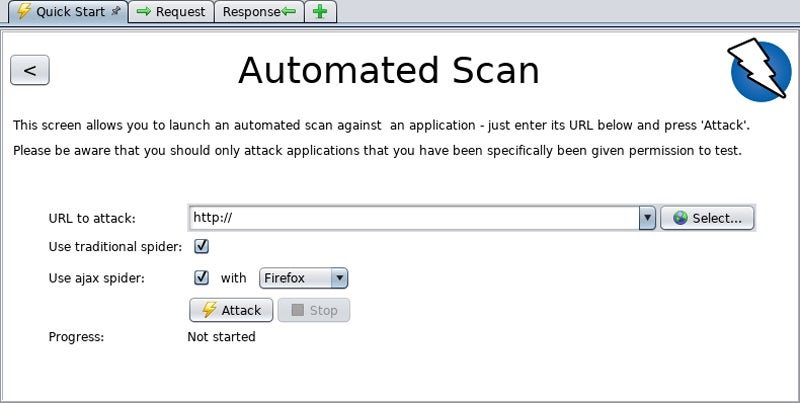
ZAP – Best Web & App Scanner Overall
Overall Rating: 4.6/5
- Open-source value: 5/5
- Core scanning features: 3.9/5
- Ease of use: 4.8/5
- User support: 4.4/5
Zed Attack Proxy (ZAP) scores the highest overall for all open-source vuln scanners and provides the highest rated open-source value and ease of use of the tools tested. Pre-installed on Kali Linux, ZAP places itself between the tester’s browser and the web application to intercept requests to act as a “proxy.” This tests applications by modifying contents, forwarding packets, and other user behavior simulations in a comprehensive and robust fashion.

Pros
Cons
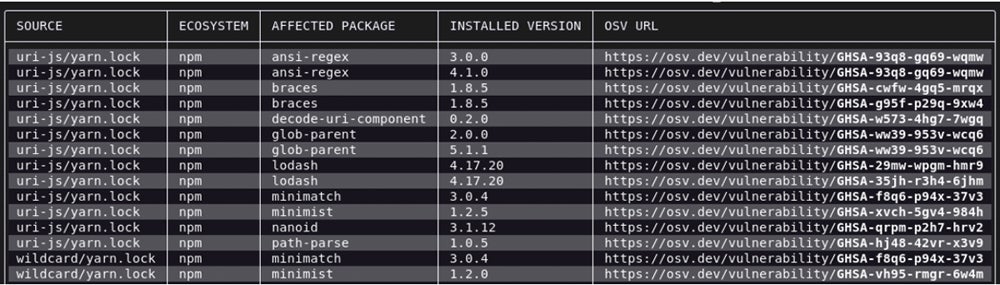
OSV-Scanner – Best Web & App Scanner for Library Dependency
Overall Rating: 4.0/5
- Open-source value: 4.7/5
- Core scanning features: 3.8/5
- Ease of use: 3.4/5
- User support: 3.7/5
OSV-Scanner delivers specialty software composition analysis (SCA) that scans static software for open-source programming code vulnerabilities to secure the open-source software bill-of-materials (SBOM). It was developed initially by Google, and the rapid development of additional features and growing number of included languages speed the adoption of the tool and enhance its industry reputation.

Pros
Cons
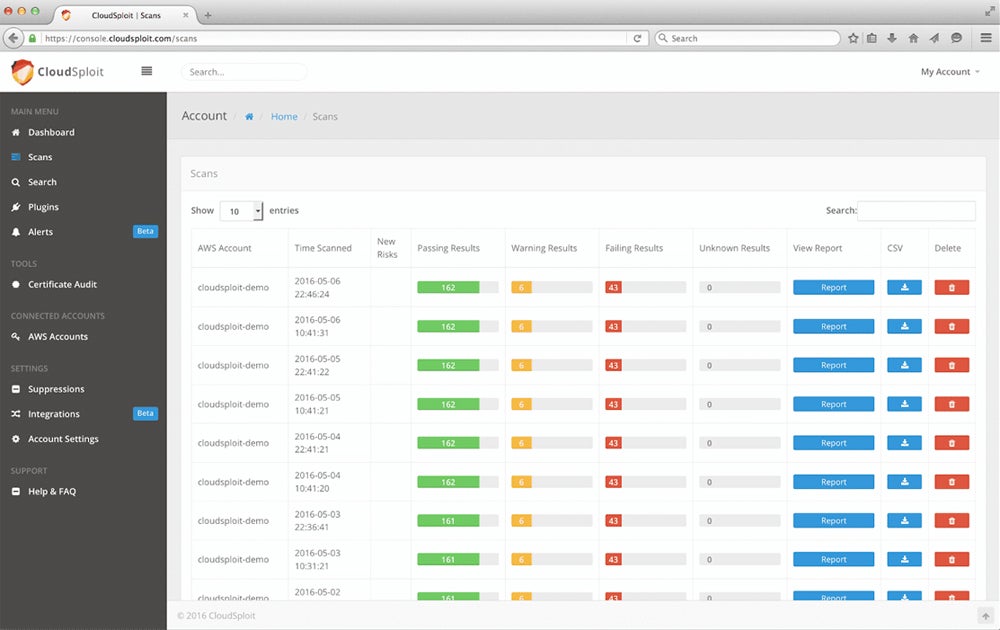
CloudSploit – Best Specialty Scanner for Cloud & Containers
Overall Rating: 3.9/5
- Open-source value: 4.1/5
- Core scanning features: 3.8/5
- Ease of use: 3.9/5
- User support: 3.0/5
Aqua acquired and continues to maintain the open-sourced cloud-infrastructure scanning engine CloudSploit so that users can download, modify, and enjoy the benefits of the specialty tool. CloudSploit scans can be performed on-demand or configured to run continuously and feed alerts to security and DevOp teams. This tool examines cloud and container deployments not only for known vulnerabilities but also for common misconfiguration issues.

Pros
Cons
sqlmap – Best Specialty Scanner for Databases
Overall Rating: 3.8/5
- Open-source value: 4.1/5
- Core scanning features: 3.8/5
- Ease of use: 3.2/5
- User support: 3.9/5
The sqlmap tool qualifies for a position on this list, with an extremely focused but capable database vulnerability scanning tool. Although limited in scope, database testing tends to be a critical component in ecommerce, card payments, and other financial services that require heavy compliance and security testing. This tool requires programming and database experience to use, but provides powerful capabilities to test for common database problems.

Pros
Cons
Top 5 Features of Open-Source Vulnerability Scanners
While very different in purpose, all open-source tools share the same features in common: asset scanning specialties, quality vulnerability scans, code available to the public, a community of professional users, and up-to-date databases of vulnerabilities.
Asset Specialization
All vuln scanners focus on specific categories of assets, such as devices, websites, and applications. Even specialty scanners tend to focus on a specific subset of these broader categories. For example, sqlmap focuses on a very specific set of tests for a sub-category of applications: databases.
Effective Vulnerability Scanning
Effective vulnerability scanners must perform rigorous scans and produce usable reports to obtain industry acceptance. Open-source scanners may be free, but their scanning capabilities must also remain top notch for industry professionals to continue their use.
Open-Source Code
To qualify as an open-source tool, the source code for the tool must be publicly published and available for review. To make this list, I incorporated the frequency and the type of updates into the scoring, so open-source tools no longer updated failed to qualify. Open-source tools may not always be free, but these top tools also all offer at least a free version.
Professional User Community
Open-source tools typically lack formal product support and instead rely upon a broad community of professionals to provide mutual product support. The top tools also benefit from inclusion in cybersecurity or hacking certification or other industry training that spreads knowledge about the tool and increases the user base.
Updated Vulnerability Database
To deliver effective scans, vuln scanners must tap into a quality vulnerability database with an updated threat feed or vulnerability list. Open-source scanners tap into public databases with constant updates and these winners often incorporate multiple public sources for improved libraries of vulnerabilities, misconfigurations, and other issues.
How I Evaluated the Best Open-Source Vulnerability Scanners
In my examination of open-source vulnerability scanners, I compared them across four categories composed of additional subcriteria related to each category. The weighted scores then generated scores out of five points for each tool and the top six tools overall made the final cut. These tools were then classified into their specific scanning categories for direct comparison: device scanning, web and app scanning, and specialty scanning.
Evaluation Criteria
In the evaluation, I weighted the open-source value the highest to favor the most regularly updated tools. The core scanning features also received heavy weight so updates and capabilities delivered 70% of the score. I also considered and evaluated ease of use and user support, but with much less weight considering the do-it-yourself nature of open-source tools.
- Open-source value (40%): Considers the frequency of code updates, vulnerability updates, if updates add features or just fixes, and the perceived quality of the scan.
- Criterion winner: ZAP
- Core scanning features (30%): Compares scanning capabilities across asset types, applications, programming languages, containers, etc.
- Criterion winner: Nmap
- Ease of use (20%): Looks at the technical level required, vulnerability management integrations, installation requirements, and the expected rates for false positives.
- Criterion winner: ZAP
- User support (10%): Examines the support available through certification training, community forums, and professional peers as well as reporting and automation.
- Criterion winner: OpenVAS
Frequently Asked Questions (FAQs)
What Are the Benefits of Using Open-Source Vulnerability Scanners?
Open-source vulnerability scanners are generally free to use and quick to download, deploy, and use. Furthermore, they tend to be used by hackers and provide an attacker’s point of view.
Are Open-Source Vulnerability Scanners as Effective as Proprietary Ones?
Open-source tools provide most of the capabilities of proprietary tools, but proprietary tools add proprietary vulnerability research, additional features, additional integration options with vulnerability management tools, and more full-service support.
Who Shouldn’t Use an Open-Source Vulnerability Scanner?
Time-pressured or less technical teams should use commercial vulnerability scanning tools or vulnerability-management-as-a-service (VMaaS) to save time or for additional help since open-source tools require technical expertise and more time to use them effectively.
Can Penetration Testing Tools Be Used for Vulnerability Scans?
Penetration testing tools such as Wireshark, Metasploit, or Aircrack-Ng can be used to conduct vulnerability scans, but these tools lack the extensive vulnerability libraries, reporting, and ticketing tool integration of a vulnerability scanning tool.
Bottom Line: Vulnerability Scans Start & Verify Security Processes
Open-source tools extend vulnerability scanning capabilities to budget-strained organizations and allow teams of all sizes to test assets and controls for vulnerabilities. To pick the best option, first consider the types of assets to scan and then compare the capabilities of the best open-source and commercially available tools and acquire the best fit. Yet even the best tool can use backup, so always consider at least one open-source alternative as a second option.
Still, knowledge of vulnerabilities only kick-starts the security process. Many vulnerabilities need verification through penetration testing, fixes need to be developed for issues beyond patch management, and then vulnerability scans must be repeated to test the fixes. Be sure to implement the full vulnerability management and remediation cycle to minimize risk exposure.
To further explore security processes to prevent attacks, read more about the differences between vulnerability scanning and penetration testing.
Julien Maury contributed to this article.