Bottom Line
McAfee Enterprise Security Manager (ESM) remains in the Leaders portion of the latest Gartner Magic Quadrant for SIEM, just behind IBM, Splunk and LogRhythm. McAfee’s licensing approach makes it a good fit for buyers looking for turnkey appliances (physical and virtual) and simplified purchases and deployments. McAfee ESM is also ideal for users of other McAfee products, for native integrations and interoperability. Gartner said ESM lags competitors in machine-driven analytics, automation, and orchestration capabilities.
Company Description
Founded in 1987 as McAfee Associates, it became Network Associates in 1997 as a merger of McAfee Associates, Network General, PGP Corporation and Helix Software. In 2004, the company changed its name back to McAfee to reflect its focus on security-related technologies. McAfee was acquired by, and was a wholly owned subsidiary of, Intel from 2011 through 2017. In April 2017, McAfee returned to being a standalone security company. Currently, it is a joint venture between Intel and TPG Capital.
Product Description
McAfee ESM includes threat intelligence feeds, correlation, analytics, profiling, security alerts, data presentation and compliance. It offers intelligence and integration to prioritize, investigate and respond to threats, while the embedded compliance framework and built-in security content packs simplify analyst and compliance operations. ESM is the core product of McAfee’s SIEM solution portfolio, which includes McAfee Enterprise Log Manager (ELM), McAfee Advanced Correlation Engine (ACE), McAfee Event Receiver (ERC), McAfee Database Event Monitor (DEM), McAfee Application Data Monitor (ADM) and McAfee Global Threat Intelligence (GTI). McAfee ESM offers integration with dozens of complementary incident management and analytics solutions, including McAfee Threat Intelligence Exchange. Based on endpoint monitoring, it aggregates low-prevalence attacks, leveraging global, third-party, and local threat intelligence.
More recently, version 11.0 has been released. It extended ESM functionality with:
- McAfee Behavioral Analytics, which provides out-of-the-box correlations for behavior-related activities
- McAfee Investigator (AI-powered incident and event investigation)
- A new open data bus architecture that shares huge volumes of raw, parsed and correlated security
- Faster ingestion and query performance
- Expanded cloud support with the addition of HVM for AWS, Office 365, Azure, Xen, Hyper-V, and a generic cloud API to more onboard new cloud-centric data sources
ESM is also one component of a larger McAfee Security Operations Platform.
See our complete list of Top SIEM tools.
McAfee SIEM Features Rated
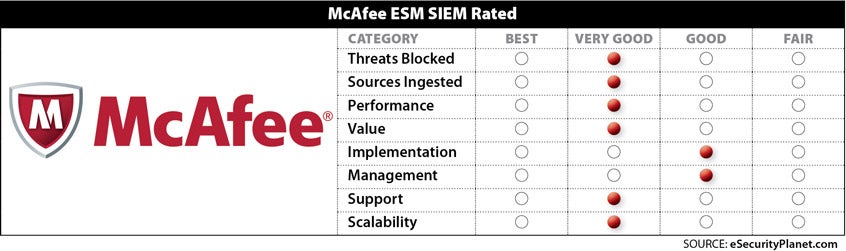
Threats blocked: Very good. Common threats or threat categories addressed by ESM:
- Reconnaissance
- Suspicious outbound traffic
- Perimeter security monitoring
- Intrusion
- Anomalous traffic detection
- Brute force attack
- Privilege account misuse
- Credential theft
- Account compromise
- Internal reconnaissance
- Lateral movement
- Data exfiltration
- Suspicious behaviors associated with advanced threats
- Denial of service
- Exploits
Sources ingested: Very good. McAfee ESM supports 430 data sources out of the box. New connectors are added monthly.
Throughput: Very good. ESM can collect large volumes of events and flow from multiple distributed Event Receivers (ERCs). Tuned ERCs can support 90,000 EPS. The SIEM architecture is designed to scale out horizontally to allow unlimited ingest and query performance. Four ESMs working in a cluster collectively could ingest an average of 2 million events per second. Query performance against 2 billion events in a database can return results against within 15 seconds.
Value: Very good. According to Gartner Peer Insights, McAfee ESM received the 2018 Customer Choice designation, making it one of six of the highest-rated SIEM products.
“We have increased our SEIM scope by 400% since implementing. McAfee does not charge by log source or EPS so you are not limited by licensing and you will start to expand your scope,” said a CIO in the retail industry.
Implementation: Good. Implementations vary substantially from customer to customer. The time required is not related to software and hardware installation, but the configuration and tuning of data sources, rules, and reports.
“The McAfee SIEM is easy to set up, add data sources, and provide usable results within hours of deploying,” said a government systems manager.
Management: Good. McAfee ESM provides methods to ingest data, manage devices, and consume data visually through dashboards and reports. Data presentation prioritizes threats with context and access to raw data, providing situational awareness and real-time response. Data source onboarding reduces the time required to configure new data sources. However, Gartner said McAfee ESM is lacking in automation and orchestration capabilities.
Support: Very good. Users are generally pleased. Standard support is round-the-clock global access to technicians for resolution of issues, via phone, email and an online service portal in multiple languages. Additional support options include professional services, training, and personalized account management.
Scalability: Very good. McAfee ESM appliances or virtual machines can be added at any point to add ingestion, query performance and redundancy. The largest customers based on appliance count and EPS:
- Appliance count in a single environment: 6 ESMs, 130 ERCs (combined virtual and hardware), and 4 ACEs
- Maximum EPS: a hierarchical deployment utilizing 20 ESMs, 18 HA ERC pairs (36), 9 ELMs and 9 ACEs
ESM devices can be clustered to support millions of events per second.
Security qualifications
FIPS 1402 level 2, CC EAL2+, listed on DoD Unified Capabilities Approved Products List, U.S. Army Information Assurance Approved Products List, approved for Navy networks, and compliant with NIST SP 80092, NIST SP 80053, NIST SP 80082 and NERC CIP007.
Intelligence
McAfee Behavior Analytics (MBA) uses big data security analytics and unsupervised machine learning to uncover unusual and highly risky behavior that is otherwise very difficult to identify. It processes vast amounts of data from multiple sources, creating a baseline of “normal” activity and a risk score for every monitored entity. ?McAfee Investigator (MI) helps analysts investigate incidents more quickly and effectively. Guided, systematic inquiry gathers supporting data, interprets evidence, and presents insights needed to fully validate threats and respond.
Delivery
ESM can be purchased as appliances or as VMs, and can be deployed on-premises, in the cloud, or hybrid. ESM supports deployments on AWS, Azure, Hyper-V, VMWare, and Xen. McAfee also provides ESM to service providers, many of whom offer ESM to their customers as a service.
Pricing
There is a more flexible pricing model for SIEM VMs, which offers licensing for each device as an eight-core VM. Users can add cores in smaller increments to an existing license. Starting price is $40,794 for one of McAfee’s all-in-one SKUs.






